Question 1
Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)#switchport port-security
2950Switch(config-if)#switchport port-security mac-address sticky
2950Switch(config-if)#switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two)
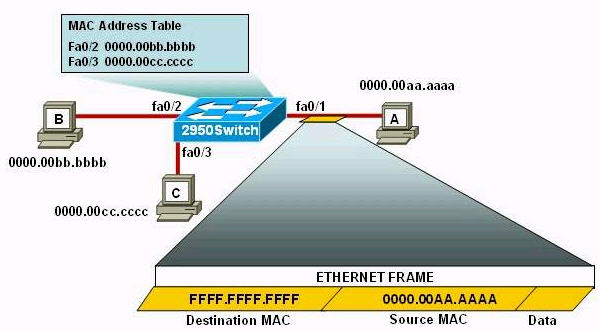
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. Only host A will be allowed to transmit frames on fa0/1.
C. This frame will be discarded when it is received by 2950Switch.
D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.
F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be forwarded out fa0/1.
Answer: B D
Explanation
Please read the explanation at http://www.9tut.net/icnd2/icnd2-operations
Question 2
Which Cisco Catalyst feature automatically disables the port in an operational PortFast upon receipt of a BPDU?
A. BackboneFast
B. UplinkFast
C. Root Guard
D. BPDU Guard
E. BPDU Filter
Answer: D
Explanation
We only enable PortFast feature on access ports (ports connected to end stations). But if someone does not know he can accidentally plug that port to another switch and a loop may occur when BPDUs are being transmitted and received on these ports.
With BPDU Guard, when a PortFast receives a BPDU, it will be shut down to prevent a loop -> D is correct.
Question 3
Why will a switch never learn a broadcast address?
A. Broadcast frames are never sent to switches.
B. Broadcast addresses use an incorrect format for the switching table.
C. A broadcast address will never be the source address of a frame.
D. Broadcasts only use network layer addressing.
E. A broadcast frame is never forwarded by a switch.
Answer: C
Question 4
Which three statements accurately describe layer 2 Ethernet switches? (choose three)
A. Microsegmentation decreases the number of collisions on the network.
B. If a switch receives a frame for an unknown destination.it uses ARP to resolve the address.
C. Spanning Tree Protocol allows switches to automatically share vlan information.
D. In a property functioning network with redundant switched paths, each switched segment will contain one root bridge with all its ports in the forwarding state. All other switches in that broadcast domain will have only one root port.
E. Establishing vlans increases the number of broadcast domains.
F. Switches that are configured with vlans make forwarding decisions based on both layer 2 and layer 3 address information.
Answer: A D E
Question 5
Switch ports operating in which two roles will forward traffic according to the IEEE 802.1w standard? (Choose two)
A. alternate
B. backup
C. designated
D. disabled
E. root
Answer: C E
Explanation
IEEE 802.1w is the standard of Rapid Spanning Tree Protocol (RSTP). There are 5 port roles in this standard: Root port, Designated port, Alternative port, Backup port and Disabled port. In these 5 port roles, only Root port and Designated port can forward traffic.
Question 6
Select the action that results from executing these commands:
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security mac-address sticky
A. A dynamically learned MAC address is saved in the startup-configuration file.
B. A dynamically learned MAC address is saved in the running-configuration file.
C. A dynamically learned MAC address is saved in the VLAN database.
D. Statically configured MAC addresses are saved in the startup-configuration file if frames from that address are received.
E. Statically configured MAC addresses are saved in the running-configuration file if frames from that address are received.
Answer: B
Explanation
The full syntax of the second command is:
switchport port-security mac-address sticky [MAC]
If we don’t specify the MAC address (like in this question) then the switch will dynamically learn the attached MAC Address and place it into your running-configuration -> B is correct.
Question 7
What is valid reason for a switch to deny port access to new devices when port security is enabled?
A. The denied MAC addresses have already been learned or configured on another secure interface in the same VLAN.
B. The denied MAC address are statically configured on the port.
C. The minimum MAC threshold has been reached.
D. The absolute aging times for the denied MAC addresses have expired.
Answer: A
Explanation
A security violation occurs in either of these situations:
* When the maximum number of secure MAC addresses is reached on a secure port and the source MAC address of the ingress traffic is different from any of the identified secure MAC addresses, port security applies the configured violation mode.
* If traffic with a secure MAC address that is configured or learned on one secure port attempts to access another secure port in the same VLAN, applies the configured violation mode.
From the second statement we can figure out A is the correct answer. But for your information we will discuss other answers as well.
Answer B is not correct because we can’t configured which MAC address will be denied. We can only configure which MAC is allowed.
We can only configure the maximum MAC threshold, not the minimum threshold -> C is not correct.
The aging times are only configured for allowed MAC addresses, not for denied MAC -> D is correct.
For your information about aging time:
When the aging type is configured with the absolute keyword, all the dynamically learned secure addresses age out when the aging time expires
This is how to configure the secure MAC address aging type on the port:
Router(config-if)# switchport port-security aging type absolute
and configure the aging time (aging time = 120 minutes)
Router(config-if)# switchport port-security aging time 120
When this command is used, all the dynamically learned secure addresses age out when the aging time expires
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)


